Everyone agrees that one of the components of the overall Internet of Things picture that needs to be tackled is security. It was clear since long before September’s IoT-based attacks and several other security incidents.
The industry knows it, businesses with IoT strategies know it and consumers know it. After the attacks (although there is not always a direct link) several IoT security initiatives were taken in all possible areas of the Internet of Things.
Cybersecurity can’t be an afterthought in IoT nor anywhere else in this age.
The challenge and state of IoT device discovery, onboarding and monitoring
IoT security is not easy and it’s different from IT security. There are other components and standards, for instance regarding connectivity, and the security approach of course encompasses IoT devices.
Obviously there are also similarities between IT and IoT security. Organizations that have a mature cybersecurity strategy work in a holistic way, focus on all components with a clear shift to the endpoints (e.g. the ‘user’) and the adoption of real-time security monitoring and cybercrime prevention approaches, even involving predictive analytics.
Knowing that the Internet of Things has several security concerns across different areas and that solving those is key for the industry, one might expect that real-time endpoint security monitoring (the endpoints in this case being the devices that get connected, or at least their sensing and data components) is an important focus for IoT security professionals.
A different approach for IoT device discovery
Yet, research from Great Bay Software, which was carried out before the September IoT DDoS attacks, shows there is still a lot to do. Moreover, another approach gets recommended.
Gartner recently stated that no IoT market segment is safe from attacks and that there is a lack of visibility (of connected IoT devices) to begin with. In a research note, the research firm said that to address this lack of visibility, IoT security products that provide device discovery, visibility and control are gaining momentum.
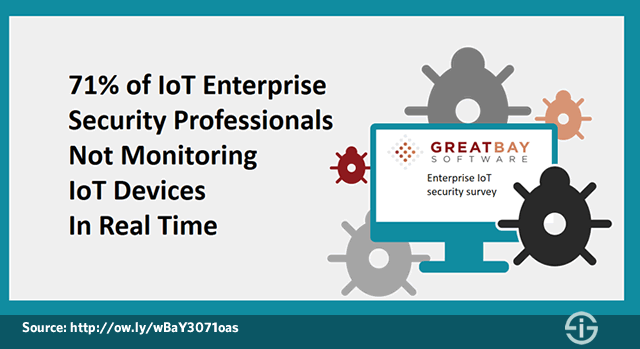
Great Bay Software mentions the research and findings of Gartner in the announcement of its Enterprise IoT security survey that showed few security professionals have a policy for visibility, discovery and classification of IoT devices in place.
Great Bay Software wanted to know about the impact of IoT devices from this IoT device discovery, visibility, classification and policy perspective and also aimed to see if behavior monitoring and network access controls for IoT devices were in place.
The poll found that 43 percent of respondents had no plans to accurately classify every IoT device on the network. 28 percent said they plan to address the issue in the next 6 to 12 months. No classification means vulnerability so at the time of the poll, 71 percent of IoT devices were vulnerable.
Traditional endpoint security and legacy network access control products do not work in most IoT use cases
When asked about plans to deploy of a solution for real time discovery, as Great Bay Software offers it as an important player in endpoint and IoT connection security, 30 percent said they have no plans now and 30 percent have plans in the next 6 to 12 months.
Gartner Research VP Lawrence Orans says that organizations may need an alternative method to address IoT security that will require being able to discover, identify, onboard, monitor and control connected IoT devices, as well as a consistent and continuous enforcement of access policies.
The reason, according to Gartner Research Director Saniye Burcu Alaybeyi: “The vast majority of IoT devices — whether connected to a wired switch or through Bluetooth, ZigBee, Z-Wave or Wi-Fi — are unmonitored and resource-constrained. They lack the ability to run traditional solutions, such as agent-based software, or they can’t be scanned remotely, thus opening new paths of attack into IoT environments. Therefore, traditional endpoint security and legacy network access control (NAC) products do not work in most IoT use cases.”
More findings:
- You can read Gartner’s recommendations in the ‘2016 Gartner Market Guide for IoT Security’, available on the website of Great Bay Software.
- The press release from Great Bay Software.
Manish Rai, VP of marketing at Great Bay Software comments: “With an estimated 25 billion IoT devices predicted by 2020, security professionals need to increase their IoT security posture and take proactive steps to get ahead of this significant emerging threat.”
And for Great Bay Software this means helping the enterprise to accurately and continuously discover, onboard, monitor and enforce access policies across all connected IoT devices.
Security and the Industrial Internet of Things
Middle image: Shutterstock – Copyright: monicaodo – All other images are the property of their respective mentioned owners.

