The increasing digitization of industrial networks comes with ample benefits. But at the same time, the attack surface of OT (operational technology) with Industrial Control Systems (ICS) grows as industrial infrastructures become more complex and Industrial IoT more externally connected. The human dimension, among others on the level of awareness, culture and needed skills remains vital in OT and ICS cybersecurity as employee errors cause half of all ICS incidents.
Increasing automation and industrial transformation lead to more complex industrial infrastructures. With organizations across ample industries embarking on a journey of digitalization and Industry 4.0 becoming more than a buzzword, the protection of industrial networks and infrastructures is more critical than ever.
Fortunately, cybersecurity has become a board-level issue according to the TÜV Rheinland Cybersecurity Trend Report 2019 we’ve covered before. At the same time the report, however, also warned that industrial cybersecurity is years behind and that especially IoT security has a standards issue. There is indeed still quite some work regarding OT and ICS cybersecurity.
The challenge at hand isn’t easy: complex industrial infrastructures require advanced protection measures and the skilled people to make them possible. But cybersecurity skills shortage is precisely a repeatedly emphasized challenge.
In its “State of Industrial Cybersecurity 2019” report, Kaspersky points out that organizations experience a shortage of professionals to handle new threats and low awareness among employees.
Digitalization of industrial networks and adoption of Industry 4.0 standards are in the pipeline for many industrial companies according to the report. Four out of five organizations (81%) see operational network digitalization as an ‘important or very important’ task ahead (this year). But for all the benefits that connected infrastructure brings, there are indeed those cybersecurity risks.
The gap between the perceived importance of OT and ICS cybersecurity and allocated budgets/resources
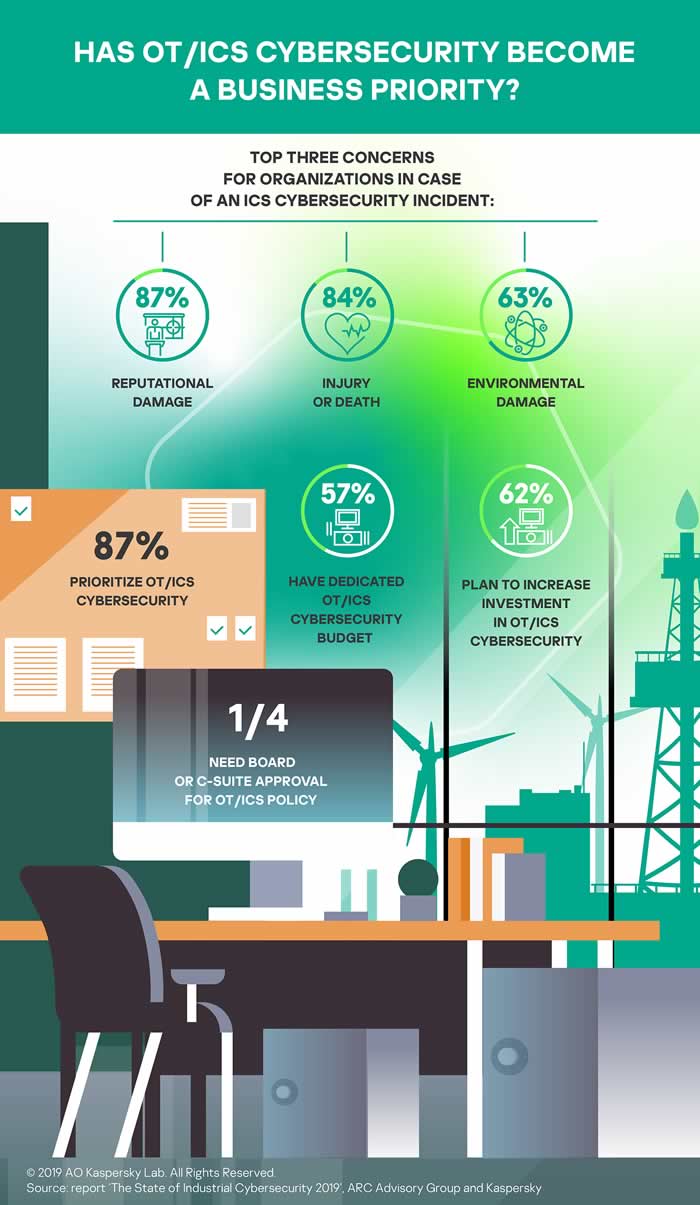
Kaspersky has good news too, precisely the same as TÜV Rheinland and several others had: OT and ICS cybersecurity is becoming a top priority for industrial companies with 87% of respondents claiming so.
Unfortunately, as we keep seeing for years now, there is a gap between what people say and do. While the vast majority says that OT and ICS cybersecurity becomes a top priority, only 57% of those polled have the allocated budget for industrial cybersecurity. As you can see in the infographic Kaspersky made, however, 62% plan to increase investments in OT and ICS cybersecurity.
Only a quarter need board or C-suite approval for the OT/ICS policy and the top three concerns for organizations in case of an ICS cybersecurity incident are, respectively:
- Reputational damage (87%)
- Injury or death (84%)
- Environmental damage (63%)
The budgets and overall resources for industrial cybersecurity aren’t nor shouldn’t be just about technological solutions, security services, and so forth. Remember that Kaspersky doesn’t just mention (new) threats but also handling low awareness of employees when it refers to the shortage of professionals.
The latter, low awareness, is indeed a challenge in industrial cybersecurity and Industrial IoT whereby we looked at Industrial IoT security awareness issues before. The human factor in OT and ICS cybersecurity can’t be underestimated, and Kaspersky emphasizes awareness in the State of Industrial Cybersecurity 2019 for a reason.
Employee errors or unintentional actions were behind 52% of incidents that affected operational technology and industrial control system (OT/ICS) networks in 2018, according to the report.
The need for more advanced protection and skills is partially a matter of investing in dedicated measures and having highly qualified professionals to make them work effectively. It is also a matter of increased awareness.
Additionally, we can’t overlook the fact that the worlds of IT and OT are still in the process of convergence, whereby different ways of working, different priorities and culture play a role as well. The examples of conflicting interests in a cybersecurity scope are known. IT might want to do security updates right away while OT might want to wait as uptime, production and so forth can’t be impacted. This issue can only be addressed on a management level.

The skills to manage industrial network protection and the awareness of OT/ICS network operators regarding the potential impact of their behavior
Back to the Kaspersky ‘State of Industrial Cybersecurity 2019’ report and what it says about skills with regards to cybersecurity. In addition to budget constraints, there is a question over skilled staff, as mentioned.
It doesn’t just mean that organizations are lacking the cybersecurity experts that have the skills to manage protection for industrial networks. Those polled are also worried that their OT/ICS network operators are not fully aware of the behavior that can cause cybersecurity breaches.
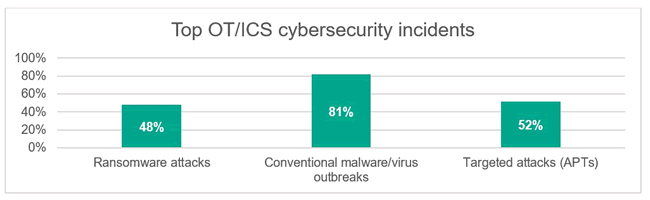
Both challenges make up the top two major concerns relating to cybersecurity management and go some way to explaining why employee errors cause half of all ICS incidents — such as malware infections — and also more severe targeted attacks, Kaspersky adds. As you can see in the graphic below, conventional malware and virus outbreaks accounted for most OT and ICS cybersecurity incidents in 2018, followed by targeted attacks (APTs) and ransomware attacks.
According to the survey in 45 percent of companies, the security of OT/ICS networks is overseen by the same people who are responsible for the protection of IT infrastructure.
Since – even if operational and corporate networks become increasingly connected, – specialists in IT and OT can have different cybersecurity approaches (which is the case according to 37%) and goals (18% of respondents), the fact that the IT security employees also oversee security of OT/ICS networks on top of their core tasks comes with security risks.
Addressing OT and ICS cybersecurity challenges
So, what is needed? Kaspersky concludes: “In addition to a technical and awareness boost for industrial cybersecurity, organizations need to consider specific protection for Industrial IoT which can become highly connected externally.”
That increasing external connectedness, among others, shows in the fact that 41 percent of respondents are ready to connect their OT/ICS network to the cloud, using preventive maintenance or digital twins.

Commenting on the research that was conducted by ARC Advisory Group, Dr. Jesus Molina, Chair of the Security Working Group within the IIC (Industrial Internet Consortium) states that the growing interconnection between IIoT edge devices and cloud services continues to stand as a security challenge.
It’s one of the reasons why the organization created the IIC Industrial Internet of Things Security Framework and the subsequent best practices documents and recent IoT Security Maturity Model. You can get all the information about these documents and models from the ICC via the organization’s website.
Click for a full version of the Kaspersky report “State of Industrial Cybersecurity 2019”
For the report and survey, conducted by ARC Advisory Group, 282 industrial organizations across the globe were polled in spring 2019.

