Software supply chain attacks are a growing cybersecurity challenge. They become increasingly frequent and can have a more significant impact, affecting many organizations at once.
Supply chain attacks are not new and fit in a broader evolution in which cyber risks and attacks increasingly involve third and even Nth parties. Third parties, among others, include suppliers, vendors, and others – such as contractors – with whom we are connected within our ecosystems one way or the other.
More than three out of every four respondents (77%) have suffered a supply chain attack (CrowdStrike)
Software supply chain attacks are a form of supply chain attacks in a broader sense. They simultaneously represent an evolution in how cybercriminals operate, whereby the way we develop software today is crucial.

Supply chain security in motion
In our increasingly connected world where digital transformation in practice often means ecosystems, we increasingly use APIs (Application Programming Interfaces) from third parties, existing components, and libraries with – usually open-source – code (think of GitHub, for example).
The number of software dependencies in the applications we buy can sometimes be vast. And when a popular open-source project or part thereof is used as a dependency and exploited to add malicious code, the consequences can be enormous.
According to the 2021 Open Source Security and Risk Analysis (OSSRA) report, open-source libraries are the foundation for every application in every industry, and open source is so prevalent that many code owners aren’t aware of all the open-source components in their software.
Supply chain attacks describe breaches stemming from compromised or vulnerable code in sources that organizations have historically trusted as secure software applications, components, infrastructure, and support and that they rely upon for current operations (CrowdStrike)
The report also found that 84 percent of codebases had at least one vulnerability, with an average of 158 per codebase. In addition, the number of vulnerabilities increased by 9 percent compared to the year before, and in no less than 85 percent of commercial software, there are outdated open source components.
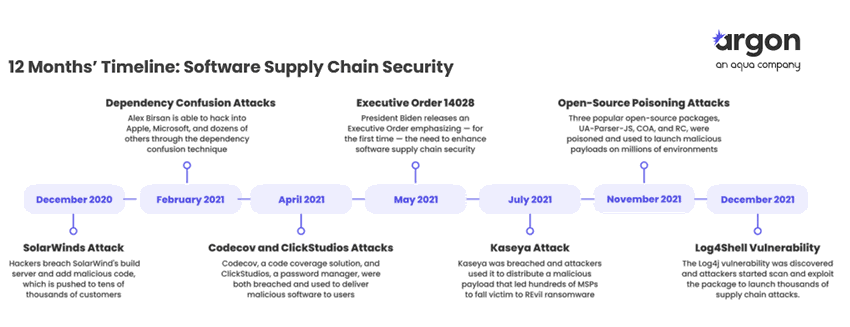
There are many known examples of “classic” supply chain attacks and software supply chain attacks. Companies are paying more and more attention to them, although there is still much work to be done.
Integrated risk management must include a software supply chain risk management part (not to be confused with supply chain risk management or SCRM, which concerns supply chain management). Software supply chain risk management starts with visibility, enabled by supply chain risk management applications. On that level, it is no different from cyber supply chain risk management (C-SCRM) as we know it from the world of IT and OT integration and Industry 4.0 or from risk management in general.
Software supply chain risk management tools go deeper than vendor risk management (VRM) and third-party risk management (TPRM) applications (or modules in broader applications).
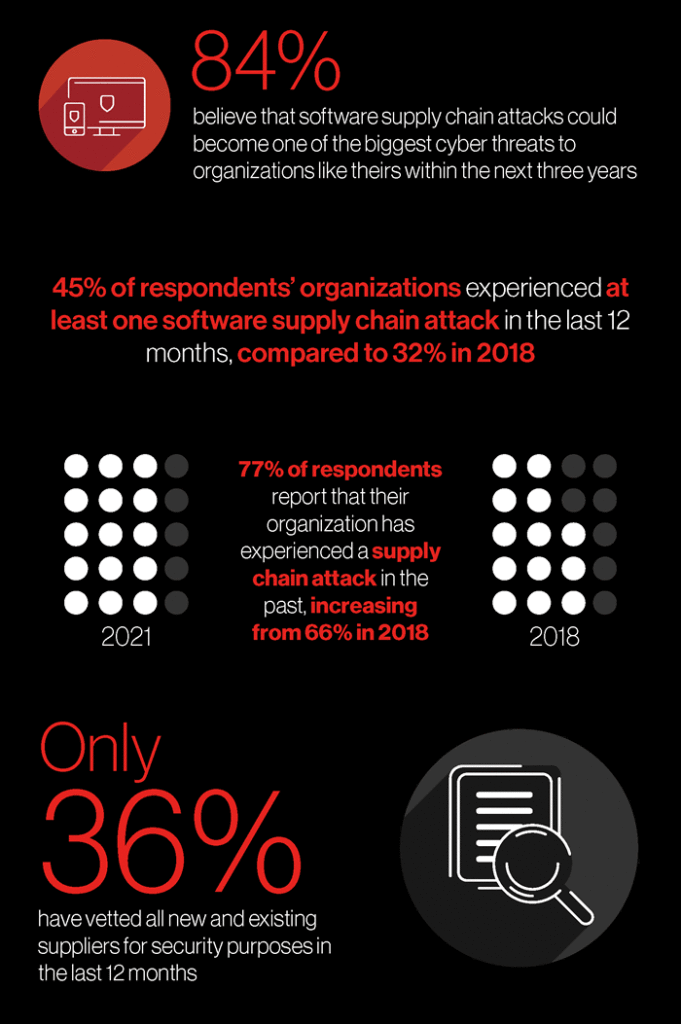
According to a survey conducted by market research specialist Vanson Bourne for cloud security specialist CrowdStrike, 45 percent of the organizations surveyed were victims of a software supply chain attack in the past twelve months.
For the report, Vanson Bourne surveyed around 2,200 senior IT decision-makers and security professionals from organizations with at least 100 employees from more than a dozen countries in the US, EMEA, and APAC regions from September through November 2021.
In some countries, the number of reported supply-chain attacks is even higher. For example, 51 percent of Dutch survey participants said they had been the victim of a software supply chain attack ‘in the past 12 months’.
The survey further found that more than a third of companies had been victims of a software supply chain attack multiple times.
Only 41 percent of affected organizations had a comprehensive strategy to deal with the attack(s). Globally, only 55 percent of IT decision-makers and cybersecurity professionals are confident in the IT security of their organization’s supply chain.
Security and DevOps teams need to collaborate in building their software supply chain security strategy and implement automated security within the development process (Eran Orzel, Argon Security)
Moreover, 72 percent of organizations do not yet hold their external suppliers to the same security standards as they do themselves. Several analysts expect this to change due to the increasing threat and awareness of (software) supply chain risks and attacks. Vanson Bourne also found a changing attitude in the survey for CrowdStrike.
For example, 78 percent of those surveyed indicated that they want to become more resilient to supply chain attacks in the next 12 months, although there are again regional differences.
The findings are more or less in line with studies that found that sixty percent of security leaders plan to deploy software supply chain security measures in 2022.
Not a luxury when we know that, according to research company Forrester, sixty percent of security incidents will come from issues with third parties, including software supply chain attacks.
A closer look at the risk areas of software supply chain security
According to Argon Security, an Israeli-origin security company that offers a “holistic security solution” to protect the integrity of the software supply chain and DevOps processes, the number of software supply chain attacks more than tripled in 2021.
In early 2022, cloud-native security provider Aqua Security, which shortly before acquired Argon Security, announced the results of a study by the company on the subject.
In the Argon 2021 Software Supply Chain Security Report, Argon Security states that attackers are most focused on open source vulnerabilities and poisoning, code integrity issues, and exploiting the software supply chain process and supplier trust to distribute malware or backdoors.
The report further found that although the number of software supply chain attacks had increased by more than three hundred percent, the level of security in software development environments remains low.
For example, every company evaluated was found to have vulnerabilities and misconfigurations that have exposed them to supply chain attacks. Argon points to several causes, such as a lack of resources, budget, and knowledge among most teams to deal with supply chain attacks.
Eran Orzel, Senior Director of Customer Success and Sales at Argon, points out that it takes collaboration between development and DevOps teams to address this attack vector. And that, of course, makes it an even more significant challenge.
Application security teams face challenges because of the sharp rise in supply chain attacks and the already mentioned widespread impact a single attack can have.
And that is the intention of the attackers. As Orzel writes in a blog post about the report, “When attackers launch a supply chain attack, they are in throwing a wide net affecting thousands of companies in a single attack.”
Argon’s study identifies three primary risk areas that companies need to understand and address to improve software supply chain security: 1) vulnerable packages usage (using the Log4j attacks as an example), 2) compromised pipeline tools (using the SolarWinds breach as an example) and 3) code/artifact integrity.
84 percent of respondents are fearful of supply chain attacks becoming one of the biggest cybersecurity threats in the next three years (CrowdStrike)
Software supply chain attacks: becoming one of the biggest cyber threats
The people at CrowdStrike expect cybercriminals could soon establish separate branches focusing entirely on supply chain attacks. The reason: the payout of a successful supply chain attack is much greater than that of an average ransomware attack.
Ronald Pool of Crowdstrike further points out that there is a growing awareness of software supply chain attacks but that many companies have outdated security requirements for suppliers or no such requirements at all.
Therefore, he recommends that these security requirements be closely scrutinized and regularly updated to meet current needs. And that, in turn, is good news for cybersecurity companies that offer tools and modules for vendor risk management and third-party risk management and for cybersecurity specialists with a holistic approach.
We see these companies going further and further in terms of functionalities, integration, and automation. The latter is also essential in an increasingly complex IT reality in which companies often have no – or not enough – visibility on their Internet-facing IT assets and the risks in a supply-chain context. Moreover, cybersecurity experts really shouldn’t be busy with manual and time-consuming tasks as their skills are needed elsewhere.
According to the 2021 CrowdStrike Global Security Attitude Survey (download), “84 percent of respondents are fearful of supply chain attacks becoming one of the biggest cyber threats to organizations like theirs in the next three years”.
Top image: Shutterstock – Copyright: Svilen G – All other images are the property of their respective mentioned owners and serve illustration purposes only.

