Among the most sensitive types of personal data are census data, data regarding religion, data about sexual orientation, financial data and, obviously, healthcare data.
Many of them are protected by specific laws and regulation across the globe, some of them by sector-specific frameworks, others by broader regulations (including supra-national ones) and several by a mix of all the above. The GDPR regulation in the EU, for instance includes virtually all possible personal health data and even genetic data.
While healthcare information and health-related data in general is protected by pretty strict laws and regulations (some call the healthcare ‘industry’ the ‘compliance industry’), the digitization of healthcare records and digital health overall require additional attention, to say the least.
The ongoing digitization of health records and digitalization of healthcare demand better security measures
This ongoing digitization of health records and of medical records (not the same) offers tremendous benefits, whether you look at it from the patient, healthcare worker, healthcare system, payers or providers perspective, at least if the main goal of the data is making healthcare information work smoothly for the benefit of the key stakeholders: patient and professional.
The digitization of health records is unstoppable. And, so, the providers of any part that is required to do it (document scanners, document scanning software, EHR/EMR systems, security solutions and so on) keeps growing, although EHR (electronic health record, the digital patient chart) and EMR (electronic medical record) are predicted to grow slower in the overall healthcare IT market.
One of the areas where investments certainly won’t slow down is cybersecurity. How else could it be?
First, there are still several initiatives to digitize healthcare records. In the UK, the NHS is pushing the paperless NHS digitization agenda and in the US we have the HITECH Act’s Electronic Patient Care Reporting (ePCR) requirements.
Next, the digitization and digitalization of healthcare doesn’t stop with medical records, patient files, test lab results and all the other types and carriers of health-related information that are sent across numerous channels in massive volumes each single day.
On the contrary: we’re still at the beginning of a range of transformations in healthcare. As an example and as we mentioned in our overview of digitization and digital transformation in the healthcare industry, both healthcare providers and healthcare payers are poised to couple care plans, premiums, benefits, reductions and so forth with, among others, data from wearables and the Internet of Things (IoT), artificial intelligence and the sharing of health data by patients.
The healthcare data protection challenges of the acceleration in emerging technology adoption
Moreover, the Internet of Things in healthcare, and specifically remote monitoring and IoT-enabled biosensors, will increasingly be used, among others in the context of an aging population. Active patient engagement is expected to lead to a growth of connected devices that track health information.
For some security experts this growing reliance on the Internet of Things (both in the consumer/patient market and in the so-called Industrial Internet of Things) and on AI is a nightmare. Yet, the predictions from IDC are clear. And, still is doesn’t stop there. Mobile health (mHealth) and wireless health are poised to grow fast until at least 2020.
We can go on with predictions and evolutions (there are far more) but it’s clear that security professionals will be very much needed amidst all these evolutions and that a simple security approach or ticking off the boxes of compliance and regulation won’t be enough.
As really should be the case in all digital transformation strategies and technology-enabled deployments, security will be a matter of security and privacy by design, embedded security and a holistic approach regarding data/information, including the digital and non-digital healthcare information carriers we’ve mentioned. And we can’t but emphasize – again – that security needs to be involved from the very start of any digital transformation – and IoT – project.
Let there be no mistake: the same people (IDC) that predict IoT and AI will ar key transformational elements for healthcare payers and healthcare providers and that by 2019 over 40 percent of healthcare organizations will use IoT-enabled biosensors predict that by 2018 (in one year) there will be twice as many ransomware attacks in healthcare. Indeed, ransomware attacks alone.
The doubled-edged sword of digitization and digitalization in healthcare – benefits and increased risks
It’s clear that in such circumstances simply checking off the compliance box isn’t enough. This is precisely what Thales e-Security says in a report, conducted with analyst firm 451 Research.
In announcing the results of the 2017 Thales Data Threat Report, Healthcare Edition, the company points out the doubled-edged sword of digitization – and we would add ‘of digitalization).
While the report covers data threats, security concerns and strategies and cybersecurity practices and spending in general, the healthcare edition looks at healthcare data security in the US, the UK, Germany, Australia, Mexico, Brazil and Japan. The announcement regarding the healthcare edition and some of its key takeaways was done at the occasion of the (past) HIMSS Conference 2017 in the US.
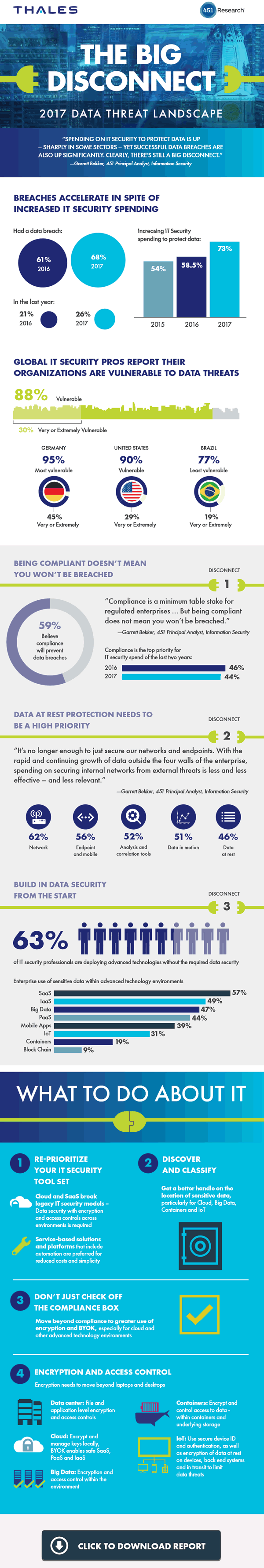
A look at some of the findings, healthcare only and predominantly US. First “the bad news” as the report puts it.
Security controls after deployment of new technologies
60 percent of US respondents who are active in healthcare stated that their organizations deploy new technologies BEFORE having appropriate levels of data security in place.
Knowing that, also according to the report 94 percent of US healthcare organizations use co-called advanced technologies for sensitive data and many are planning deployments across several of these new technologies that is not exactly good news indeed.
In the scope of the evolutions we mentioned regarding the Internet of Things and healthcare, it’s interesting to note that the top 5 of these ‘advanced technologies’ are, respectively (in decreasing order of usage), Software as a Service (SaaS) as the obvious leader, followed by Big Data, IaaS (Infrastructure as a Service), mobile and PaaS (Platform as a Service).
So, no IoT yet, as it ranks sixth with 30 percent of respondents. As we saw that could change fast and if we then would see the similar pattern of having appropriate data security controls in place AFTER deployment in many organizations, the consequence is: major troubles ahead.
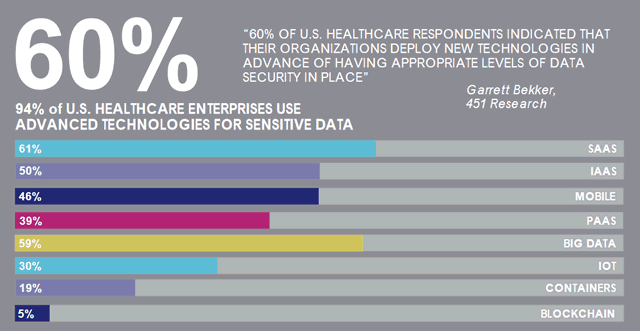
More healthcare security investment but more data breaches
Bad news part 2: both in the US and globally, data breaches are up (also in general, beyond healthcare as you can see in the infographic at the bottom) despite the increase in security spending to protect data.
Moreover a major percentage of security professionals in healthcare across the globe state that “their organizations are feeling some level of vulnerability to threats to sensitive data”. Globally, 88 percent feels vulnerable to data threats, in the US 90 percent does so.
This probably won’t come as a surprise and we would like to point a few things out here:
- First, if indeed many healthcare organizations first deploy and then have the right levels of security it’s quite obvious many are vulnerable.
- Next, we need to correlate these findings with the growing number of attacks (remember the prediction of IDC: double as much ransomware attacks in healthcare in one year) and the fact that cybercrime is up in all sense of the word: volume, sophistication, etc.
- Thirdly, increasing security spending to prevent healthcare data breaches doesn’t necessarily mean that this spending is done properly. We do live in an age where a holistic and end-to-end view on embedded security by design matters and the security perimeter hasn’t just shifted to the endpoints but to ALL parts of the overall data and security risk picture.
The sub-optimal security investment prioritization in healthcare
The fact that healthcare organizations are poised to spend even more on protecting healthcare data is good news.
Globally (or: in the surveyed countries), there is a significant increase in the spending to protect data. The less good news though is that spending is growing least in technologies which are perceived as most effective in protecting sensitive data and growing faster in some rather ‘traditional’ types of defense that are perceived as less effective with regards to protection of sensitive data.
Other good news is the fact that a significant percentage (43 percent in the US) never had a data breach or data security compliance failure, that compliance and preventing data breaches top the list of US healthcare IT security spending priorities and that compliance, dubbed ‘a minimum table stake for regulated enterprises”.
The mixed picture of health data protection compliance – and need to move beyond it
While compliance is indeed essential for regulated enterprises and, we would add, for the protection of patients who in the end matter most, just being compliant of course is no guarantee there won’t be breaches as the report points out.
Putting compliance at the top of healthcare security priorities appears to help US healthcare the press release further states.
However, there is something weird going on with compliance. In “the rest of the world” (read: the UK, Germany, Australia, Mexico, Brazil and Japan) compliance is only a healthcare IT security spending priority for 20 percent of respondents, making it rank after the prevention of data breaches (39 percent), which on the other hand could also be seen in the scope of compliance, and several other spending priorities. In the US, on the other hand, compliance is cited as an IT security spending priority for 57 percent of respondents.
While we’re not too familiar with the situation in the LATAM and APAC regions, we do know that in the UK, in Germany and in many Western-European countries compliance de facto is driving the cybersecurity agenda. So, it would be interesting to see more data in this regard.
If it turns out that, in contrast with what we see, compliance is indeed less of a priority in, for instance, Germany, we would be pretty surprised as Germany has been way ahead of many other (European countries) in data protection rules. As an example: in Germany data protection officers already exist (they are an obligation under the GDPR which applies to companies processing personal data of EU citizens and patients in 3 cases).
We wouldn’t exactly call the GDPR (and laws in some European countries) less stringent. On the contrary: the GDPR alone is VERY stringent with regards to sensitive personal data and healthcare data. Of course, the UK is heading for its Brexit but still. If compliance is not on top of the agenda in European countries then this can only mean one thing: the lack of awareness and preparedness regarding the GDPR is even bigger than we thought.
Encryption, ability to locate data and reprioritization of the IT security tool set (and approach) as ways to go beyond compliance
Talking about the GDPR – and good news: encryption is playing a larger role in healthcare data protection the Thales report found.
The press release about the ‘healthcare edition’ states that “the technology is the clear choice for satisfying local data privacy laws such as the EU’s General Data Protection Regulation (GDPR) by 66 percent of global healthcare respondents”. Encryption is also clearly favored by the GDPR (the text is clear about that).
Yet, again: compliance is key but securing healthcare data is much more than just checking off the compliance check boxes. On top of encryption, the report among others mentions the need to:
- Reprioritize the IT security tool set.
- Being more capable with regards to the location of sensitive data, among others for the cloud, Big Data, containers and IoT (note that this capability is simply a must to be GDPR compliant).
- Moving encryption beyond the computer across the data center, cloud, Big Data, IoT and so forth.
- From the health data threat report PR: “deploying security tool sets that offer services-based deployments, platforms and automation” (part of reprioritization).
- “Leveraging Bring Your Own Key (BYOK) technologies for the cloud and other advanced environments”.
More in the infographic (full and larger version in PDF; also about more than healthcare data), in the recommendations which you find in the presentation regarding the report (with a section on healthcare) and in the report itself (registration required).