Penetration testing is a security method whereby ethical hackers are asked to break into predefined IT systems or applications for specific cybersecurity purposes you decide. Organizations often combine this security assessment method, also known as pen testing (some prefer pentesting), with other means such as attack surface management whenever the context/scope requires it.
Pentesting, which also includes vulnerability scanning, is evolving. This has to do, among other things, with high demand, new technical possibilities, the acceleration of digital transformation, the increasing complexity of IT and digitalization, and the greater need for an integrated cybersecurity approach.

We’ll cover some of these trends and their impact in this article and examine why organizations use pen testing (and thus pentesters conducting, indeed, pentests).
What is penetration testing? Simulating a cyber attack to improve your security
First, we take a brief look at what penetration testing is and its use. Penetration testing is a testing method and process to assess and analyze the security posture of a network, system, or application.
It is one of several methods available to organizations to assess and analyze their security posture that fits in a holistic cybersecurity strategy, aiming to enhance the security posture by leveraging gained insights.
A penetration testing definition by NIST: “Security testing in which evaluators mimic real-world attacks in an attempt to identify ways to circumvent the security features of an application, system, or network. Penetration testing often involves issuing real attacks on real systems and data, using the same tools and techniques used by actual attackers.” (NIST SP 800-115 under Penetration Testing)
In pen testing, the pentester looks for vulnerabilities and uses them within the framework of the assignment and agreements to see how they can be employed to penetrate your system/network/application.
The pen tester puts himself in the shoes of an (ethical) hacker and looks at how the confidentiality, integrity, and availability (CIA) of your data can be impacted and how flaws/vulnerabilities of a system or application can be abused to do so or cause other forms of damage.
In short: penetration testing is an intensive process involving several steps and simulating an attack on your organization. The fact that penetration testing is a simulation doesn’t mean that it’s just testing some scenarios and reporting results. Typically, pentesters will use the same tools and tactics that malicious hackers utilize to attack your systems, albeit to improve your security obviously.ating an attack on your organization.
Penetration testing is used in different ways and at various times. It is often a part of the analysis phase in more complete security efforts of companies that are starting to improve cybersecurity and want to take actions thanks to insights relatively fast.
Penetration testing goes beyond vulnerability scanning to use multistep and multivector attack scenarios that first find vulnerabilities and then attempt to exploit them to move deeper into the enterprise infrastructure. Since this is how advanced targeted attacks work, penetration testing provides visibility into aggregations of misconfigurations or vulnerabilities that could lead to an attack that could cause serious business impact. As a minimum, penetration testing provides a means for prioritizing the highest risk vulnerabilities. (Gartner)
It is also organized recurrently, whereby a snapshot of the situation is taken at specific times. Note that pentesting can be used for various systems and things such as networks, mobile applications, the Internet of Things and OT (operational technology), and more.
Pentesting can also be done more or less continuously, among others with novel approaches, as we’ll cover in a piece on trends and evolutions, including PTaaS (more below). In general, automated penetration testing gets better, but you will always need people, no matter how good it gets.
Techniques such as vulnerability scanning and (external) attack surface management ultimately serve the same purpose as penetration testing: improve security based upon analysis and insights (from data to information, knowledge, and action as in the good old DIKW model). But they also all have their limitations and – of course – advantages. That is also a reason why they are used together.
Research (more about it below) shows that the primary goals organizations pursue with pen testing are respectively assessing/analyzing the security posture and preventing breaches.
From a methodological viewpoint, a penetration test will often look at the cyber kill chain from the attacker’s perspective and follow the MITRE ATT&CK framework steps.
Penetration testing and vulnerability assessments
The combination of penetration testing and vulnerability scanning and assessment, part of vulnerability management, is relatively common in large-scale pentests because it’s part human expertise and part tools to find ways in. There is always some vulnerability scanning in the broader and deeper context of somewhat extensive penetration testing.
After all, as mentioned earlier, with penetration testing, we detect vulnerabilities and use them to allow our ‘white hat’ ethical hackers to carry out a cyberattack, as it were.
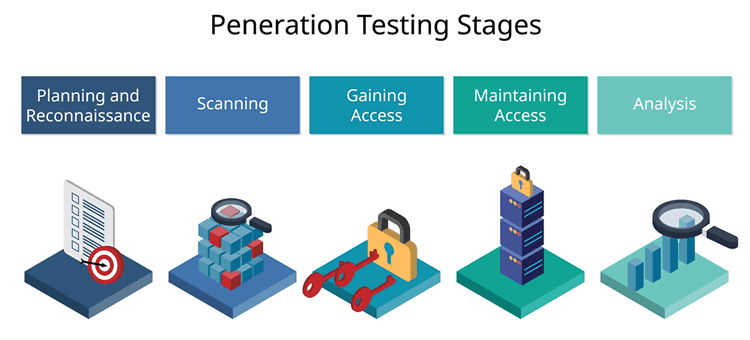
The usually far-reaching exercise, which penetration testing is, shows organizations who use it what attackers can exploit. So, pentesting is a security assessment method that takes hackers’ point of view.
The outcome of a pen test consists of a comprehensive overview of the findings and insights with grades and suggestions to address the detected problems.
Because penetration testing is so intensive and is done using various types of cybersecurity experts, it is typically, depending on the scope (and method), more expensive than vulnerability scanning and attack surface scanning.
79 percent believe that pen tests are costly. 78 percent would utilize pen tests on more apps if the costs were lower.
Do note that quite some parts, nevertheless, are automated. We also see the rise of Penetration Testing as a Service (PTaaS), among others, for automation and costs, although there’s more about it that we’ll cover in a separate article.
Also, note that vulnerability scanning isn’t just part of a penetration testing exercise. It is also often seen as a layer of cybersecurity testing, with vulnerability scanning being the first layer, penetration testing the second, and red-teaming the third.
Penetration testing and the growing attack surface
The combination of penetration testing and attack surface monitoring and management is becoming increasingly important. Pen testing, attack surface monitoring, and vulnerability scanning are three major components of security testing (with red-teaming sometimes added). So why are the attack surface and external digital footprint important in the evolution of penetration testing?
One of the often-heard comments regarding the limitations perceived in a penetration testing context is that with pentests (and vulnerability scanning), you often miss (large) parts of your external digital footprint and attack surface – and thus assets. Also, think about third-party risks and attack vectors that we ‘see’ less often in this connected and complex world of digital ecosystems as supply chain attacks are on the rise.
Research by Informa Tech, commissioned by attack surface management and protection specialist CyCognito, clarifies why penetration testing is best combined with attack surface management. The report confirms that organizations still significantly invest in and rely on penetration testing for security.
The responses from the security and IT professionals who participated in the study show that they primarily perform penetration testing to measure their security posture (70 percent of respondents).
The second most important reason, with about the same number of respondents (69 percent), is to prevent breaches. This is followed by ensuring compliance with regulatory mandates (65 percent).
Penetration testing and the evolution towards more integration
The survey indicates that today’s most commonly used pen testing approach fails to accurately reflect the degree to which the just-mentioned objectives are met.
The reason is that, on average, the tested attack surface is relatively small. For example, only 38 percent of the participants test more than half of their attack surface annually.
As the research indicates again, organizations don’t have enough visibility regarding their external or Internet-exposed assets. And when performing penetration tests, one is left with many assets that are not tested and where attackers can make their move.
“There is very limited value in testing only a portion of your attack surface periodically. Unless you are continuously discovering and testing your entire external attack surface, you don’t have an overall understanding of how secure your organization is. If there is a path of least resistance, attackers will find it, and find a way to exploit it.” (Rob Gurzeev, CEO and co-founder of CyCognito)
According to the study, the main concern regarding pen testing, as it is usually done, relates to limited test coverage and too many blind spots (60 percent). Furthermore, 47 percent of the participants stated that pentests only look at known assets rather than discovering previously unknown or “forgotten” assets, which is precisely one of the reasons why attack surface management has become so important.
Of course, and as mentioned earlier, none of this makes pentesting a ‘bad thing.’ But, as mentioned, it is all about how one does it and how things get integrated.
So it should not surprise that more vendors effectively go for integrated solutions or ecosystems, which allow for a more holistic approach. And in practice, various methods are also combined, regardless of the exact tools and choices of strategy.

